
A friend wrote for advice, as she has believes she might face unwarranted harassment for some work of hers that’s going to be released. She wondered how she could best secure everything to do with her online identity before someone manages to wriggle inside her defenses.
Most people are reactive, waiting until a bad event to take action—whether total loss of data in a hard drive crash, or an account being hijacked. It’s great she was thinking about this ahead of time, and the advice I offered her is useful to everyone who finds themselves in that position, or just wants a security tune-up.
Contents
Tune up
Mac and iOS users are often a bit smug about the security of their devices. (I know I can be.) But because of Apple’s architecture, there’s little to nothing you can do in iOS, and little to nothing that’s useful in OS X.
Primarily, these good habits will serve you well: Don’t open email you don’t recognize, and if you do, certainly don’t click any links or open any attachments. Don’t click links on dubious-looking websites. Don’t accept messages in iOS or OS X to install custom profiles when you haven’t sought them out. Being less credulous may waste some of your time, but avoid obvious problems.
The exploits that have affected Apple’s operating system in the last year were such that generally there was nothing you could do to avoid being taken advantage of. That sounds depressing, except that most of them also had obscure vectors, making them hard to implement in practice—and none were discovered “in the wild” or in forms that could spread rapidly.
What you can do in OS X, however, is install software that monitors what is talking to your computer and what service your computer is accessing. I’ve used an older version of what’s now NetBarrier X8 in the Internet Security X8 package from Intego, and Objective Development’s Little Snitch. While I don’t find any real value in anti-malware software, seeing what your system and software are up to can be reassuring.
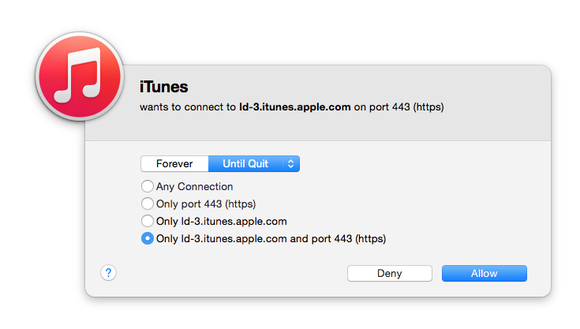
This is also useful when you’re on networks you don’t know and trust, so you can see the kinds of behavior originating from the network around you—and potentially alert a café owner or a store manager if you see someone engaged in malicious activity.
Further to this point, using a virtual private network (VPN) whenever you’re outside your comfort zone—which can include some kinds of activities on your home network—effectively locks down your Internet traffic to anyone who can intercept data over a local Wi-Fi or ethernet network and at points between that and the other end of the VPN connection in a data center somewhere. I’ve tested and can recommend both Cloak and TunnelBear, which offer varying packages and combos for limited or unlimited data and multi-platform support with a single account.
None of this assures that people can’t break in, but it reduces points of weakness, and that’s always good.
Lock down
Everywhere you can, enable two-factor authentication (2FA) or token-based logins. As I’ve written about many times, most cloud-based and social-networking services now offer some variant of it. I use Authy to manage my Time-based One-time Passwords (TOTPs), which Google, Slack, Amazon, and other outfits offer. Some will only or optionally let you use SMS. Apple’s 2FA, upgraded last fall, relies on sending information to iOS or OS X devices registered to the same Apple ID, and using SMS or voice as a fallback. (After months of trying to get my Apple ID to support 2FA, I was finally able to disable the older two-step verification and enable 2FA.)
A second factor prevents someone who obtains or guesses your password from using that from anywhere in the world to log into your account. If your services offers login alerts, which warn you whenever a new device is added or a login occurs, enable that too.
Check all social networking, email, financial, and other services you use beyond 2FA to examine privacy options. Some networks will let people who have some information about you find out more, or look you up by email address, even if there’s no public listing that associates you. They may be able to let a friend of a friend to obtain your phone number or physical address; you might consider wiping that data or further restricting it.

I also recommend changing your passwords comprehensively across all services you use. While it’s a pain, if you either can’t recall the last time you swapped a password, or you use the same password at multiple sites, the time is ripe. I recommend a password management and sync system (I use 1Password) both to create strong, unique passwords and to let you access to them whenever you need them on whatever platform you’re using. (1Password’s creators, AgileBits, have both family and business sharing options that can help you distribute passwords multiple people need; it’s great in families where spouses or parents/kids need to have access to the same password, too.)
Many hacks start with a weak link. That’s often a disused email address that you set or still use as a backup address at another service. To break into the more-important service, a cracker will poke at these weak links, break into an email address, then use a password reset or another option that allows them to use the email access as a knife to crack open the oyster of the service. So recheck all your backup/alternative email addresses associated with all your accounts as well.
Finally, while these aren’t per se computer related, I recommend you contact your cellular provider and your local home phone carrier (if you have one). You can typically put a lock or extra protection on phone accounts; they’re often a vector for attackers who use social engineering or online account management to try to shift your phone number, texts, or other services elsewhere, which can aid in identity fraud, accessing private information, or intercepting an SMS second factor.
Along these lines, you should also pull your credit reports at the three major credit bureaus, and consider putting a freeze on credit checks and issuance for every member of your immediate family. Opening cards in your name and other tricks to ruin credit is a common strategy for harassers. You should also look around for ratings of credit-monitoring services. I have free access to one after an online account breach, and it’s reliably informed me of all (so far legitimate) activity on my credit reports.
It’s no fun to worry about these sorts of things, but it’s also a reality of our modern day. If you’re concerned you might be targeted by a political, criminal, or social group, preparation will save heartbreak.
[Source:- Macworld]

