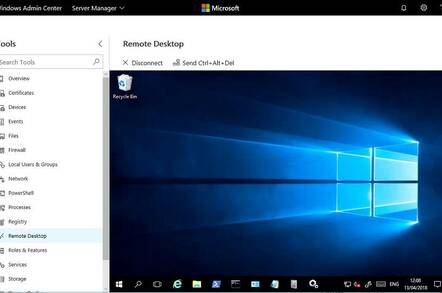
Hands On Microsoft has released Windows Admin Center (formerly known as Project Honolulu) to general availability.
Windows Admin Center is a browser application for managing servers and computers on a Windows network. What’s the point?
The answer is that browser-based administration is a logical step in Microsoft’s continuing efforts to promote remote server administration rather than the old-school approach of logging on to a GUI desktop to see what is wrong. It also brings together a number of different management and troubleshooting tools into a single user interface. Third, it promises to be a coherent central point of management for organisations too small to run System Center, Microsoft’s suite of enterprise administration tools.
Microsoft describes Windows Admin Center (WAC) as an “evolution of inbox management tools”. It does not replace any part of System Center, nor the cloud-hosted Operations Management Suite. It may replace Server Manager, the desktop GUI for managing local and remote servers, but not all the individual tools that currently run in the Microsoft Management Console, and included in the bundle called Remote Server Administration Tools, since it does not include all their features. There is no additional cost for WAC.
The company has not invented a new way of managing Windows servers. Under the covers, Windows Admin Center uses Remote Powershell and WMI (Windows Management Interface) over WinRM (Windows Remote Management), tools which have been around for years. Knowing this helps you when WAC does not work as expected.
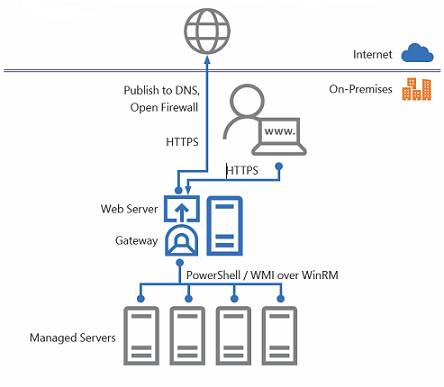
How Windows Admin Center works
This means there is no need for an Admin Center agent as such, though it does require at least PowerShell 5.1 on the target machines, which you install as part of the Windows Management Framework 5.1 or higher. Server 2016 and Windows 10 already have this version, but earlier versions of Windows may need upgrading.
Installing Windows Admin Center
There are two modes of installation. You can either run WAC on Windows 10, so you can spin it up as required, or on Server 2016 where it runs as a service and is always available. For this hands-on I took the latter path. WAC does require a trusted certificate, for which I used a domain Certificate Authority. I encountered a bizarre issue documented as “Certificate thumbprint displayed in MMC certificate snap-in has extra invisible unicode character.” Why can the installer not just present a list of installed certificates and let you select the one you want? This is the thing with Windows administration: sometimes it is delightfully straightforward, sometimes it leads you down all manner of twisty little paths.
Once installed, you open up a browser (must be Chrome or Edge) and start adding servers. You can also add Windows 10 computers (though this is not covered in the current documentation), Failover Clusters and Hyper-Converged Clusters (this tool described as a production-ready preview). A Hyper-Converged Cluster is one that uses Storage Spaces Direct in Server 2016.
All computers which you want to manage with WAC must have remote administration enabled. Before adding a Windows 10 PC, for example, I had to run winrm quickconfig from an administrative command prompt.
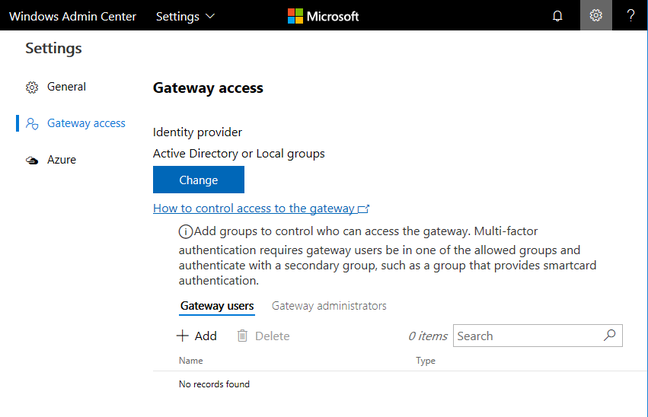
You can select groups using Azure or local Active Directory (Click to enlarge)
You can also integrate WAC with Windows Azure. You can have users authenticate to WAC using Azure AD accounts, manage Azure VMs, and setup Azure VM protection, using Azure Site Recovery. Unfortunately I have not yet got this working. You download a PowerShell script called New-AadApp.ps1, which asks for your Azure log-in and then creates an Azure application to which your gateway talks. In my case I suffered a variety of errors. Eventually, after setting up a new Azure administrator, I ran the script successfully. Trying to set up VM protection though only gets me a blank browser window. And my gateway still says it isn’t yet registered with Azure Active Directory. Never mind.
Presuming it works, configuring WAC for Azure AD authentication is a valuable feature, letting you use features including multi-factor authentication and conditional access policies, which allow you to restrict access based on location, device, sign-in risk and more. If you use local Active Directory you can require smartcard authentication.
Permission to access WAC does not give you permissions on the various servers being managed. You can enter separate credentials for each connection, or use one set of credentials across all connections. I found WAC prone to asking for new credentials even when I thought they were right, a typical Windows issue.
source:-.theregister.

